Extracting firmware credentials with binwalk and hashcat
Many embedded devices have weak default credentials that can easily be recovered from the firmware. In this post we’ll take a look at the firmware from an outdated IoT device. This is for research purposes, as part of a security audit of embedded devices. The author takes no responsibility for what you do with this knowledge. Any misuse of this will not be the responsibility of the author.
That being said, with binwalk we can examine the firmware’s contents. What we’re looking for is the file system.
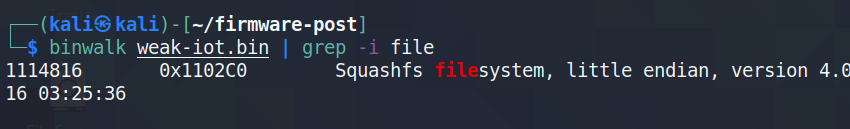
We’re in luck and the squashfs file system is right there. Next we just need to extract the contents with binwalk -e <file_name>.
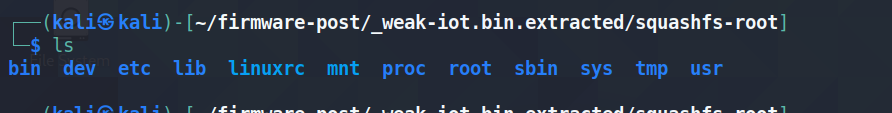
Looking inside it, we see that it’s a pretty basic Linux file structure.
Just like with any other Linux system, we can cat the contents of /etc/passwd and /etc/shadow to get a look at the
credentials.
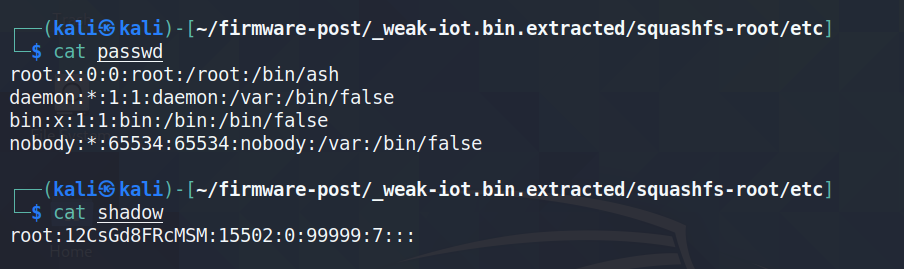
The only thing interesting is the password hash for the root user in the /etc/shadow file.
Looks like it uses DES algorithm, which isn’t common due to it being rather weak for storing credentials.
If we check the options for hashcat, we see a module for DES (Unix).
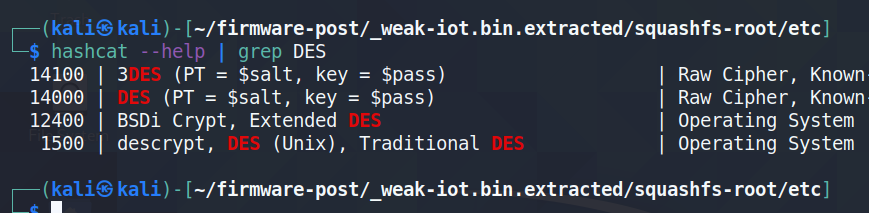
We can copy the hash to a file and run hashcat to crack it. In my case it only took about 3 seconds to crack, that’s including starting up hashcat.
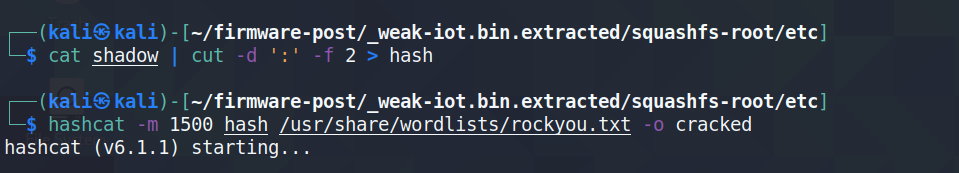
And checking the output file, we see it was indeed a very weak password: password
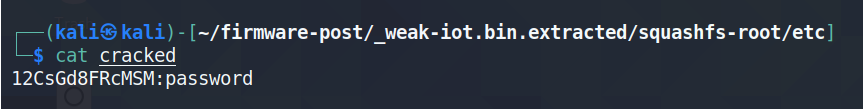
Unfortunately this is more the rule than the exception as far as default credentials in embedded devices go. It’s worth taking a look at any IoT devices you might be using, and you’ll see that the password defaults are likely not much better. As always, take a good look at the devices before you start connecting them to your network.