Auditing Linux with Lynis
When setting up a new Linux machine, one of my favorite tools to use Lynis by Cisofy. Lynis is a free and open-source auditing tool for Linux and Unix-like systems that is quick and easy to use.
In this post I’ll show how to set it up on a Debian 10 virtual machine. First step is to get Lynis; it’s as easy as cloning the repo with Git:
git clone https://github.com/CISOfy/lynisAnd then running the audit script from the Lynis repo directory:
cd lynis && ./lynis audit systemYou can also run the command as root, but will receive a warning from Linux, which is very appropriate given we are running user installed files as root. I’m going to run a privileged scan anyway, use your own judgement on your system.
A Lynis audit scan on a new system will naturally generate many warnings and recommendations as many of the settings are still using the system default. I´ll focus on some of the more common issues.
- There is a warning about the lack of password protection for the GRUB bootloader
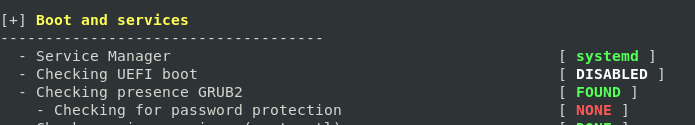
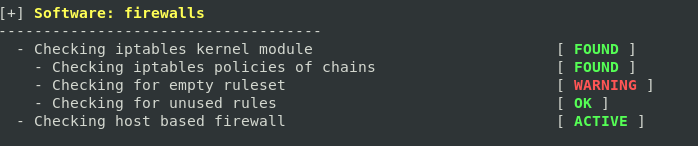
- Another warning for the empty firewall ruleset (Lynis detected iptables, but no rules have been configured)
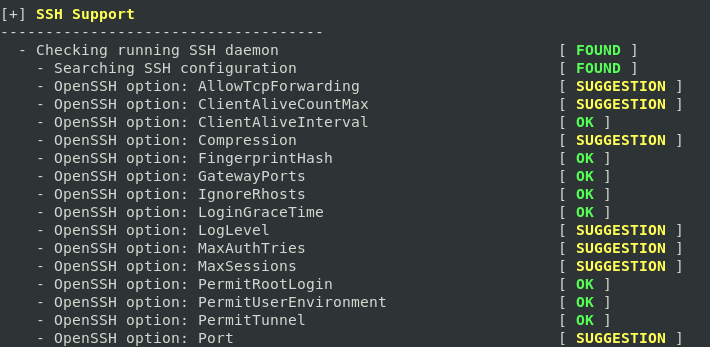
- Multiple suggestions for improving the security of the default SSH server configurations
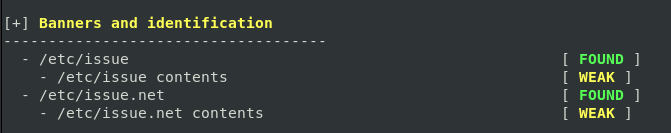
- And suggestions to configure a banner for the machine
At the end of the scan we can see Lynis generated an overall score of 62.
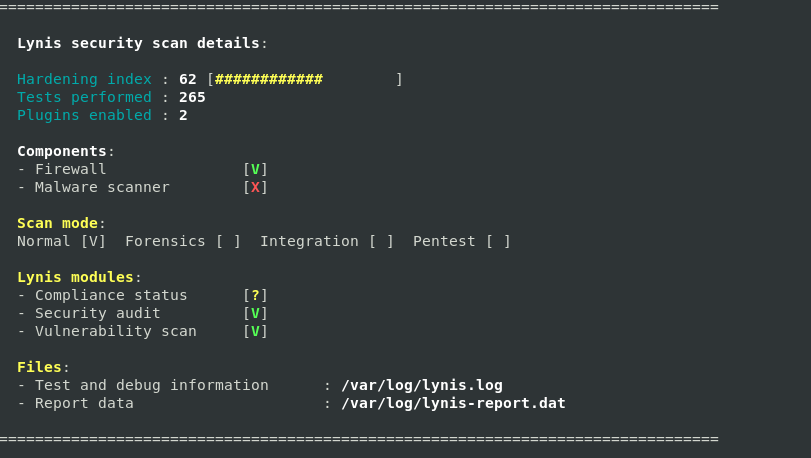
In the next section we’ll address some of these issues and see if we can improve that score a bit.
Implementing Lynis suggestions
Near the end of the scan results Lynis provides detailed explanations of many of the warnings which make updating most issues relatively easy. Let’s start with the empty firewall ruleset.
Firewall
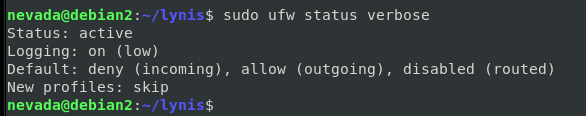
An easy way to set up a firewall on a Linux machine is with UFW (Uncomplicated Firewall). It can be installed with apt,
apt-get install ufwAnd once enabled, it will create ‘deny incoming’ and ‘allow outoing’ rules by default.
sudo enable ufwAny configured rules can be seen with the ufw status verbose command
GRUB
Next we’ll set a password for the GRUB loader, to prevent it being used to bypass the password proctected user accounts and open a root shell.
-
First thing is to generate a new password for GRUB, using the
grub-mkpasswd-pbkdf2command. Make note of the generated password hash. Also, you may want to back up these config files, messing up the GRUB configuration can be a pain.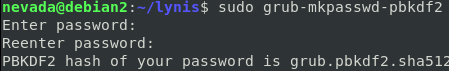
-
Then find the relevant configuration files inside of
/etc/grub.d, in my Debian 10 installation the file we need is/etc/grub.d/40_custom. It’s as simple as setting a superuser and adding the password hash generated before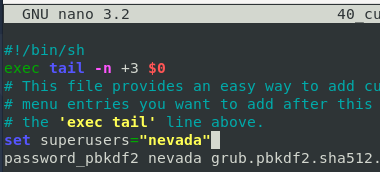
The config can be regenerated with sudo grub-mkconfig -o /boot/grub/grub.cfg, and we can see it requests a password:

Banner
By far the simplest step. Just adding the appropriate content to /etc/issue and /etc/issue.net.
Something simple like this would be fine:
##############################################
ALERT! You are entering into a secured area!
All connections are monitored and recorded.
##############################################
In the SSH settings defined in /etc/ssh/sshd_config we can set the value for the Banner setting to /etc/issue.
After restarting the service we can log in and see the new banner:
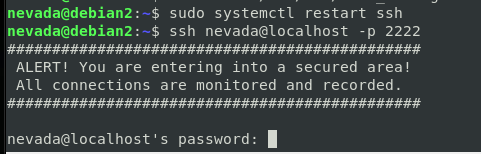
SSH settings
The details from the Lynis audit contain multiple recommendations for improving the security of the SSH server running on the machine.
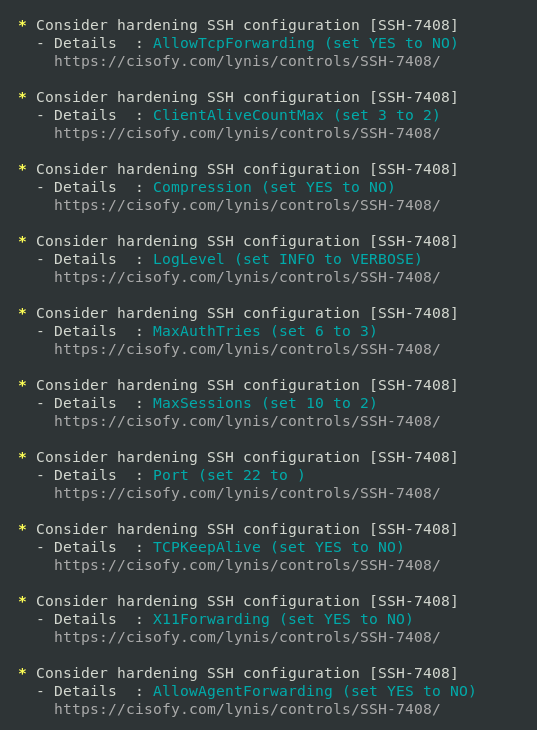
The settings for the ssh service that need to be updated can be found in /etc/ssh/sshd_config. It’s quite easy to make
the recommended changes
Rerun the Lynis audit
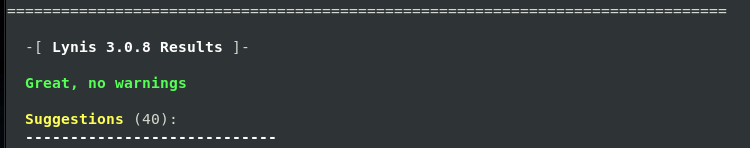
Running the Lynis audit again shows some improved results, firstly no warning!
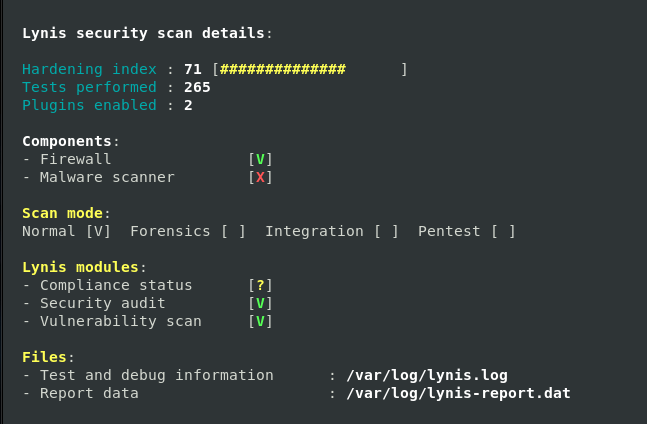
And our overall score has increased a bit to 71
Conclusion
While this is just scratching the tip of the iceberg that is server hardening, we can see that Lynis is an easy to use tool, that is useful in finding some of the more common misconfigurations on Linux systems.